Overview
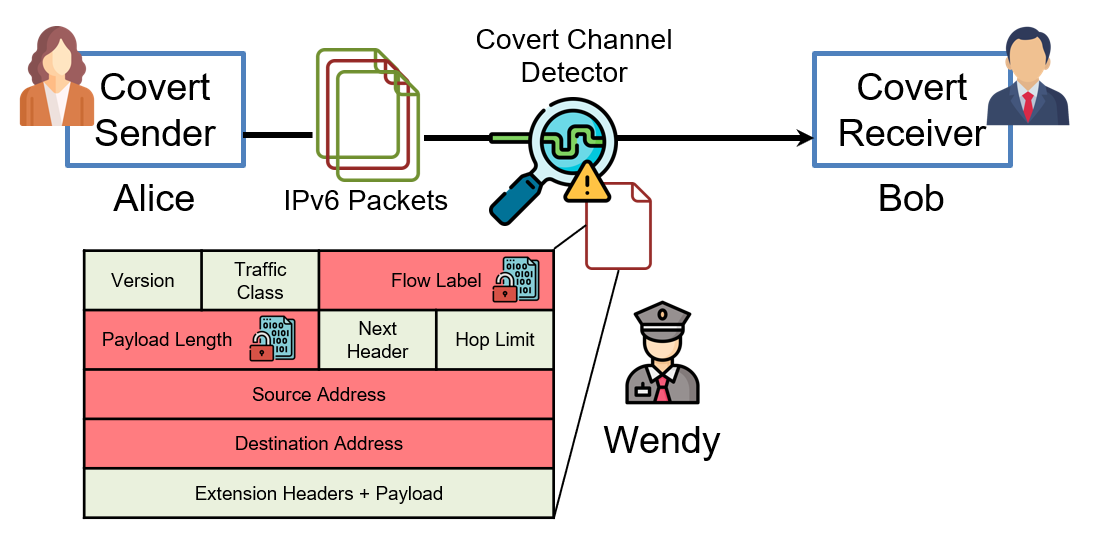
Fig: The prisoner’s scenario with IPv6 covert communication
This project introduces a state-of-the-art detection framework for covert communications in IPv6 networks, leveraging advanced Artificial Intelligence (AI), Machine Learning (ML), and Generative AI methodologies. The system is designed to address the vulnerabilities of IPv6 extension headers, which can be exploited for stealthy data transmission. By integrating neural network architectures, data encryption techniques, and generative AI for iterative refinement, this framework enables high-accuracy detection and classification of covert communication. This end-to-end solution combines data-driven insights, packet structure analysis, and dynamic AI model adaptation to mitigate modern cybersecurity threats effectively.
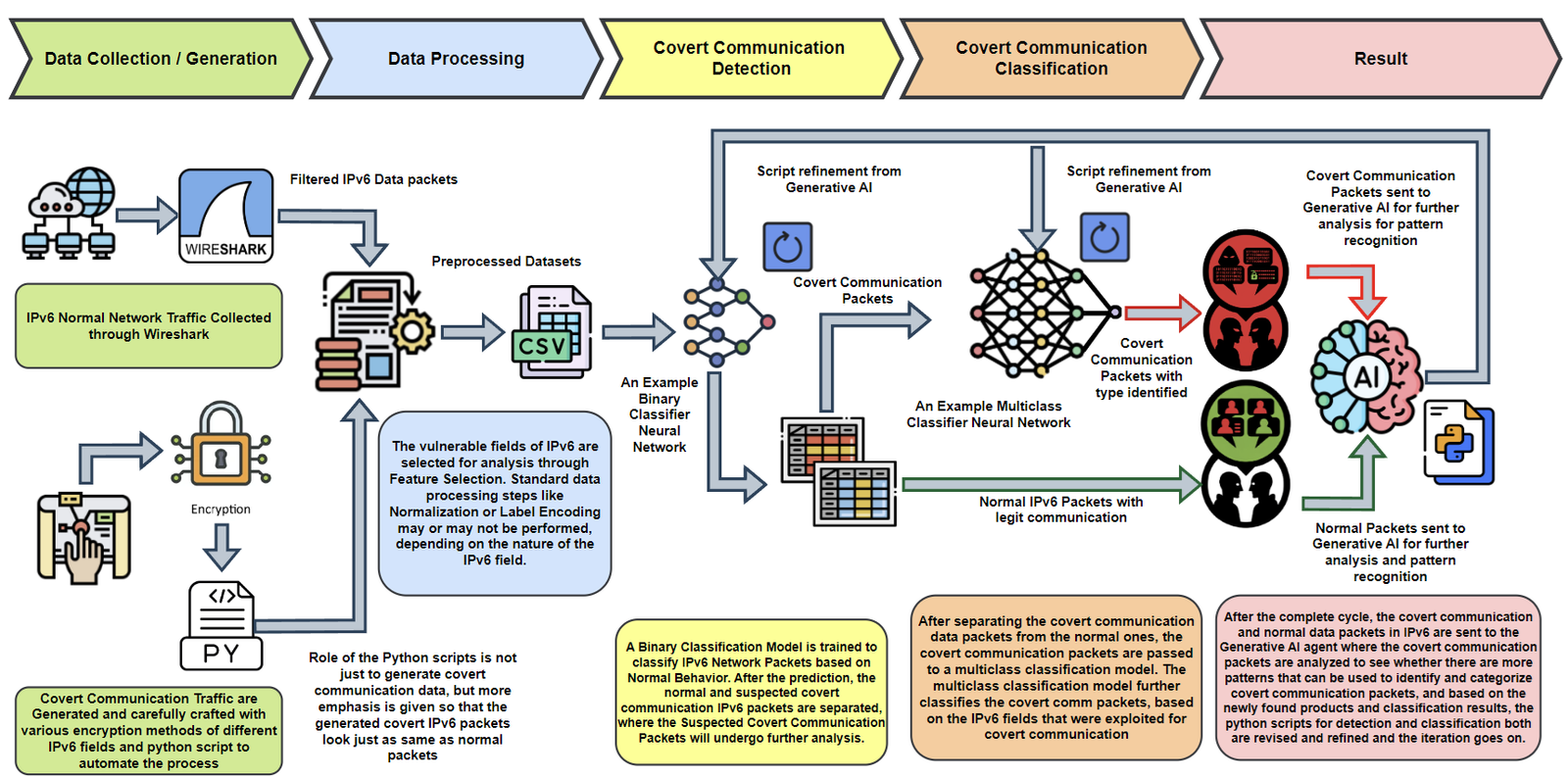
Fig: IPv6 Covert Communication Detection and Classification Framework
System Architecture and Workflow
- Data Collection & Preprocessing Phase
- Input: IPv6 packet data from real-world network traces and synthetic covert traffic.
- Processing: Data is filtered, anonymized, and structured for training and testing.
- Output: A comprehensive dataset containing normal and covert packets, enriched with encrypted header fields like FlowLabel, Address Space, and Length.
- Covert Communication Detection Phase
- Binary Classification: Identifies whether a packet contains covert communication.
- Models: Employs Random Forest, Gradient Boosting, CNN, and LSTM for robust detection.
- Output: Labeled traffic streams categorized into normal or anomalous classes.
- Covert Communication Classification Phase
- Core Algorithm: Multiclass classifiers identify the type of covert communication based on manipulated IPv6 fields.
- Processing: Explores sequential dependencies and field-specific anomalies using models like Bidirectional LSTM.
- Output: Detailed classification of covert packet types, including FlowLabel manipulation, Address Space encoding, and Length field encryption.
- Dataset Augmentation Phase
- Encryption Techniques: Generates covert packets using RC4 encryption for realistic simulation of attack scenarios.
- Dynamic Data Generation: Adapts covert traffic patterns to mimic real-world attack vectors, ensuring diverse and challenging datasets.
- Output: High-quality datasets that improve model training and evaluation robustness.
- Generative AI-Assisted Refinement Phase
- Integration: Utilizes GPT-4-turbo to iteratively refine detection and classification scripts.
- Capabilities: Dynamically selects machine learning models, optimizes code, and adjusts classifiers based on performance thresholds.
- Output: Continuously improved scripts and models achieving detection accuracy exceeding 90%.
Key Features
- Advanced Covert Communication Detection:
Employs ML models like Random Forest, CNN, and LSTM to detect anomalous IPv6 packets with high precision. - Multiclass Covert Traffic Classification:
Classifies covert packets based on encrypted IPv6 fields, enabling targeted anomaly detection. - Realistic Dataset Generation:
Synthesizes covert traffic that mimics real-world attacks, bridging the gap between research and practical applications. - Iterative Model Refinement with Generative AI:
Automates script improvement and model selection to optimize detection accuracy and resilience. - Dynamic Visualizations:
Provides interactive graphs to display traffic trends, classification results, and covert communication patterns.
Tools and Technologies
- Machine Learning Models: Random Forest, XGBoost, LightGBM, CNN, RNN, LSTM.
- Neural Network Frameworks: TensorFlow, PyTorch.
- Encryption Algorithms: RC4, Advanced Data Masking Techniques.
- Data Analysis Tools: Wireshark, Python (NumPy, pandas, scikit-learn).
- Data Sources: CAIDA IPv6 Traces, Custom Synthetic Data Generators.
- Generative AI: GPT-4-turbo for code refinement and iterative improvement.
Outcomes and Impact
- Performance Improvements:
- Achieved 95% F1 Score in binary classification tasks.
- Attained 99% F1 Score for multiclass classification of covert communication types.
- Increased detection accuracy for complex attack scenarios by 20%.
- Cybersecurity Benefits:
- Strengthened IPv6 networks against covert communication attacks.
- Enabled automated, scalable detection processes for enterprise-level security systems.
- Reduced dependency on manual anomaly detection by integrating AI-driven solutions.
- Generative AI Impact:
- Enhanced detection scripts iteratively, reducing model optimization time by 30%.
- Improved adaptability of classification models to dynamic traffic patterns.
This project presents a groundbreaking solution for IPv6 covert communication detection and classification, combining the latest advancements in AI, ML, and encryption techniques. Its comprehensive framework, from realistic dataset creation to iterative generative AI refinement, offers a scalable and effective defense against emerging cybersecurity threats. By aligning detection methods with real-world attack scenarios, this research bridges the gap between theoretical models and practical network security applications.
